This article discusses in brief about the effectiveness of Kaspersky Endpoint Security Cloud during a test conducted by AV-TEST.
Kaspersky Endpoint Security Cloud is one the many products by Kaspersky, a global security company founded in 1997. Other well-known products by Kaspersky are Kaspersky Antivirus and Kaspersky Internet Security.
If you ever decide to buy a good cyber-security program for you office, you can consider Kaspersky Endpoint Security Cloud as one of your options. Since we are also a Kaspersky Partner, you can reach us or snap up with us.
Now, if you think this article post is techy, don’t worry, as long you know that Kaspersky Endpoint Security Cloud is a good choice for your organization to protect from Ransomware attacks.
According to a recent assessment by AV-TEST, an independent research institute for IT security, Kaspersky Endpoint Security Cloud demonstrated 100% efficiency against ransomware attacks.
As a result of three different scenarios and 113 attack samples, the product didn’t lose a single user file and outran 10 different cybersecurity vendors. This is not just impressive protection for the workplace, but also an important safety net for consumers who are at risk of falling victim to these malicious attacks.
Over the last few years ransomware has grown as an industry, with plenty of malware families and gangs dedicated to it as well as attacks-as-a-service. Attacks-as-a-Service , Malware-as-a-Service and Fraud-as-a-Service are all terms commonly used for providing of illegal activities by cyber criminals.
In the second quarter of this year, almost 3,000 new ransomware variations were created and 97.000 users were attacked across the globe. This is about 6.000 more than in Q1 of this year according to Kaspersky’s research.
AV-TEST examined 11 endpoint protection platforms for three scenarios:
-
-
real-world ransomware attacks on user files stored in a local system,
-
real-world ransomware attacks on user files located in a remote shared folder, and
-
Proof of Concept of ransomware attacks on user files on a local system.
-
During the testing phase, it was expected that the products would identify, block & eliminate ransomware from your machine. The study included 25 different ransomware families, such as REvil, Ryuk, Conti, Lockbit, pysa, Ragnarlocker and Ransomexx. 14 proof of concept vulnerabilities were also presented for the test.
Kaspersky Endpoint Security Cloud successfully protected all computers in all three test cases and did not encrypt any important data. Kaspersky Endpoint Security Cloud scored the highest protection rate across all products tested, proving its value for businesses against this type of attack. It was able to protect business data in an employee’s desktop.
Cybersecurity has become a challenge as technology continues to advance. With the constantly changing threat landscape, it is difficult to identify and stop attacks. Even if there are advanced monitoring systems in place, sophisticated attackers can spend up to 146 days in a system before being detected.
For more information about Kaspersky Endpoint Security Cloud, please call us at 012-3075896.


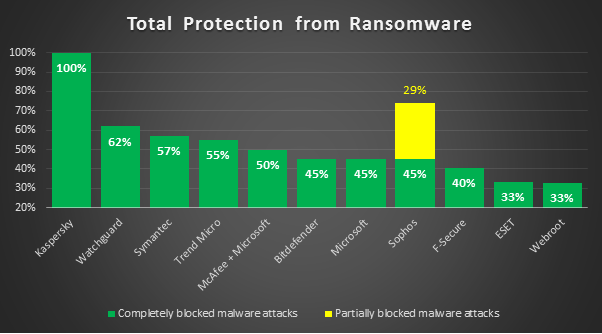 Source: Kaspersky USA
Source: Kaspersky USA