the Basic Story about SSL
As more and more people get online, consumers are starting to look for safe ways to get their information. One of the ways is using SSL, a protocol for encrypting your data on your website.
Encrypting your data is a way for website owners and consumers to protect their information. Encryption is the process of turning information into code that can’t be read or understood by anyone except the intended recipients. It’s usually used when sensitive information (like credit card numbers) is transferred over the Internet.
If you want to create a secure website, then you have to know that SSL or also knows as SSL Certificates have become an essential part of the internet. It is not only about the security but also about branding and credibility. Before you can purchase an SSL Certificate with us, it is important to understand what this certificate actually does.
The internet is an unsafe place. SSL certificates play an important role in keeping user data safe and secure. SSL helps to prevent attackers from creating a fake version of the site, which could lead to phishing or other attacks to steal user information.
Now, if you don’t have an SSL certificate, your website may still function, but it will be vulnerable to hackers and Google will warn visitors that your website is not secure.
Where do you use SSL?
It’s usually used when sensitive information. You use SSL when you have websites that have:
-
-
- Payment transactions such as credit card transactions.
- Logins such as system login web forms.
- Data Transfer such as file transfer.
-
If there is any more to add, please do share it with me at the comment section.
Why do you need to know the difference between HTTPS and HTTP?
Yes, the latter is without the “S” alphabet.
When you deploy SSLs to your websites, you would notice only https. If you go to any websites from established brands and companies, they would have https. It is very important for you to be aware about this.
Before diving deeper, it’s important to understand the difference between HyperText Transfer Protocol Secure (HTTPS) and HyperText Transfer Protocol (HTTP). HTTPS is the secure form of HTTP, and HTTPS websites are websites that have their traffic encrypted by SSL.
However, many users won’t notice the difference between an http:// and an https:// web address, but most browsers have started tagging HTTP sites as “not secure” in more noticeable ways, attempting to provide incentive for switching to HTTPS and increasing awareness.
What is SSL?
It is a security technology for establishing an encrypted link between a server and a client – typically a web server (website) and a browser (Chrome, Firefox etc) – in order to protect communication.
SSL certificates are vital to the security of website owners and consumers. It is an online security measure. It is a tool of standard for ensuring the data security are always untouched and undamaged.
When you have a website, the first step to securing your website is by installing an SSL certificate. All your URLs will need to be changed from HTTP to HTTPS in order for your server to communicate with it properly and that your user data, like login and financial information, is encrypted. This secure link ensures that all data transferred remains private
What is the difference between SSL and TLS?
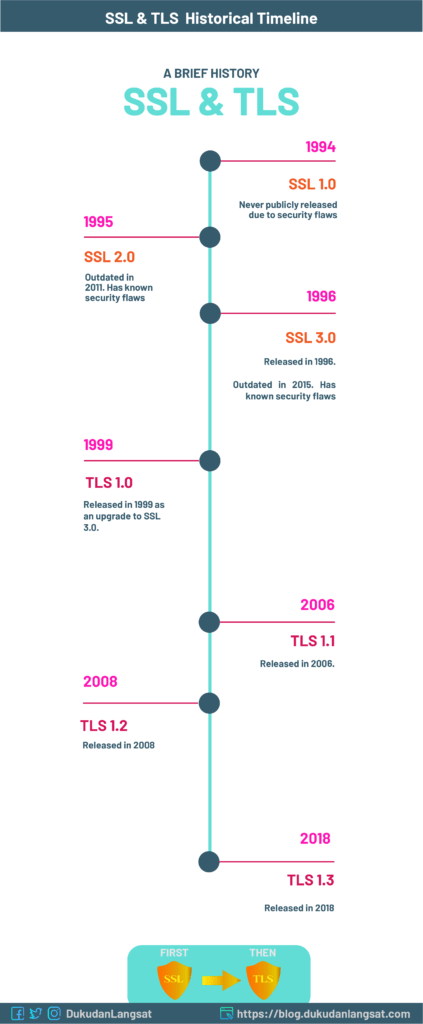
Transport Layer Security (TLS) is the successor protocol to SSL. In another words, TLS evolved from Secure Sockets Layer (SSL),
In another words, Transport Layer Security (TLS) protocol is actually just an updated version of the Secure Sockets Layer (SSL) protocol. TLS fixes some security vulnerabilities in SSL.
The terms are used interchangeably. However, people are still preferring to utilize SSL and I have used SSL in this article too. Hope, it clears your confusion.
That is all for now.
You may be interested: A historic timeline of SSL to TLS



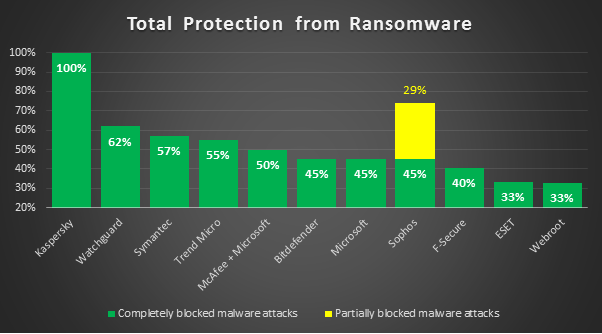 Source: Kaspersky USA
Source: Kaspersky USA